Start here!
This is a gentle introduction to getting set up and started.
I’m nowhere near as good at this as I want to be, but I’ve been inspired by a couple wizards: Bob the Ward and Paul the White.
The first thing you need to do is go download WinDbg (or the debugger of your choice — I use this one to emulate my heroes).
If you want a lot of reference material, there’s a Stack Overflow post with a list of resources, like cheat sheets and tutorials.
I should probably read those, huh?
Debuggery
Once you’ve got things installed, you’ll wanna crack the correct tool open. For most of you, that’s gonna be the x64 version.

The important thing when opening it up is to right click an run as administrator.

If you choose the wrong bits, or you don’t run as administrator, debugging won’t work.
Symbols of the Bug
The next thing you’re gonna need is some symbols.
I’m lazy, so I’m going to create a folder on my C: drive called “symbols” — then I’m gonna use that to point WinDbg to, so it can store the public symbols that Microsoft lets us plebeians use.
If anyone wants to send me the private symbols, I won’t tell.

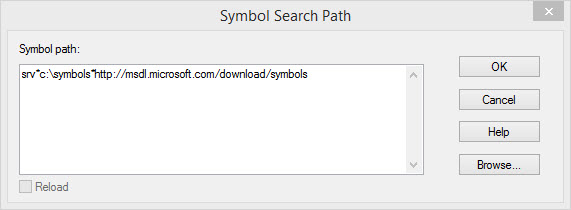
The command in here is srv*c:\symbols*http://msdl.microsoft.com/download/symbols — you’ll need to change the c:\symbols part to wherever you chose to create your symbols folder.
Action Man
Now comes the fun part! Especially if you’re not on a Mac. Or Linux. This blog post has probably been awful for you, if you are.
Let’s attach this thing! The easiest way is to either hit F6, or go to File > Attach to a process.
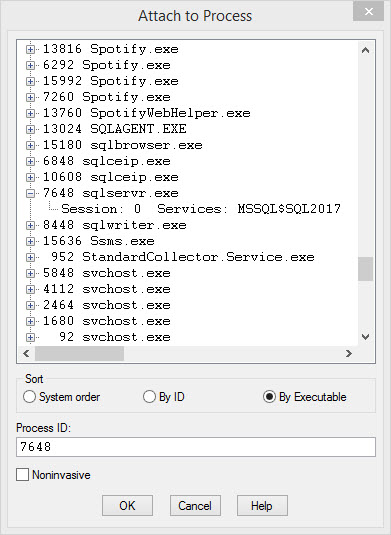
I find it convenient to sort by Executable and then scroll down to SQL Server. There are fancy command line ways to do this as well, but this is the lowest barrier to entry.
Now, remember when I said you had to choose the right bits and run as admin?
This is why! If you don’t see Session information here, or you get access denied/request can’t be completed errors when you try to attach, you did something wrong.
If you did everything right, the debugger will attach, and you’ll get a screen full of nonsense.
That nonsense will be a list of .dlls that you can get symbols for. Symbols are kind of like translators. You may not need them, but hey.
Free stuff.
To get symbols for a dll just type something like x sqllang! or x sqlmin!
If you’ve done things right, your symbols folder will start to fill up.

Closedown
That was just enough to be dangerous!
I’ll be covering some of the basics of setting breakpoints and whatnot down the line. In the meantime, poke around on your own.
Explore the space.
There’s almost no shortage of EULAs you can break stuff you can find poking around in here.
Thanks for reading!


5 Comments. Leave new
This almost feels like information I shouldn’t have! Still going treasure hunting though, thanks!
Looking forward to more.
It does feel that way, but the symbols are all public, and Microsoft distributes the software. Kinda hard not to go looking.
Couldn’t agree more. Thanks for lighting the way!
[…] True Professional could use WinDbg (the cool kids pronounce it “wind bag”) or another debugger to step through the code of […]
If you’re just after the call stack, then you can use this little piece of wizardry (which is even easier) for resolving the function calls from SQL symbol files:
https://github.com/microsoft/SQLCallStackResolver
Thanks to Jonathan Kehayias for pointing it out and to Arvind Shyamsundar for writing it.
(Gone are my days of struggling with windbg just to figure out what function calls were in the stack dump.)