What you need to do: log into SQLpass.org and change your password. If you use the same password anywhere else, change it on all of those sites immediately as well.
Why you need to do it: anytime you ever logged into SQLpass.org or SQLsaturday.com, or updated your password, or created an account, your password (along with everything else) went unencrypted between your computer and PASS’s web servers. Anyone sniffing network packets along the way saw your username, email, password, etc in clear text. (Think about what a security gold mine this would have been for someone sniffing WiFi at a SQLSaturday or the PASS Summit.) There’s a nice side benefit for updating your account – you also become eligible to vote in the current PASS elections.
Who you need to thank: the vulnerability was discovered by George Stocker on Friday, and PASS HQ finished the fixes & testing on Saturday. That’s a fantastic turnaround time – kudos to PASS for reacting so fast!
Who you should blame: yourself, for not noticing for years that you were putting login information into a web site that wasn’t using https. What kind of data professional are you, anyway? You’re probably even using that same password on multiple web sites, or heaven forbid, your company email. Get it together and use 1Password or LastPass.
Who you should not blame: the current PASS Board of Directors because this has likely been in place ever since PASS set up their current web site, and the current management inherited this little surprise. (You know how it goes – it’s like your ancient SQL Server 2000 in the corner where everybody knows the SA password.)
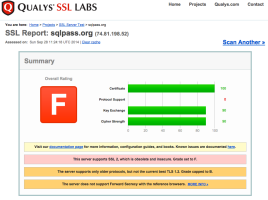
What’s still left to do: PASS needs to clearly, concisely communicate the severity of this issue to members as well – I really wish they’d set all passwords in the database to null, and force everybody to go through the password-reset process. The SSL setup still needs some work, as shown in the SSL tests, but considering the whole thing was done in 24 hours, it’s one heck of a good first step. (SQLsaturday.com also fails that test.)
Where to go for more information: logged-in PASS members can ask PASS public questions in their blog post comments, email info@sqlpass.org privately, or ask questions here in the comments.


13 Comments. Leave new
As far as I know, there is no supported way to do a global password reset using DotNetNuke. It can be done through the interface user by user. There are unsupported ways to do this:
http://www.dnnhero.com/Forum/forumid/5/postid/348/scope/posts
KBK – and hey, whaddya know, it’s just an UPDATE statement, hahaha! We can do that, we’re database pros.
Actually, there was an person that said in reply to one of your tweets that he pointed out that SSL cert was missing from website years ago to PASS…so I wonder what happened to that notification. So I think maybe this was recognized as an issue only because of your active social media pushing…and using an SSL cert is only a start. I think bigger issue is how the service provider stores the data because is there is an hole, it will definitely be an gold mine for hackers, because they can dig it even when I am offline..l suggest using professional pentesters and security professionals that can bullet proof the service. And that is the responsibility of PASS to get it done. Also remember that it can actually be https tunnel between client and front end (F5/Netscaler etc) and http tunnel to the background services.
BTW. I think I would like having https tunnel here too :/
JMont – yep, a few people have come forward to say they notified PASS about the lack of HTTPS years ago.
I agree, a security review would make sense here. There’s plenty of volunteers in this community who would love to help.
It isn’t said enough: Without your social media pushes, this may not have been fixed. You may be a bird plucking their whiskers, but it’s needed.
I wish it weren’t. I wish large organizations (this isn’t just PASS) retained the same sense of kinship towards us that they ask us towards them.
Kudos to PASS for turning around those fixes so quickly.
However (you knew this was coming), we need this sort of transparency in all their dealings, not just when they get egg on their face. DBAs represent the keys to the kingdom — if any professional group of people should be transparent, it’s the ones that have the keys to everything.
George – awww, thanks sir.
Every morning since the news broke, I’ve woken up, thought about the situation, and thought, “I need to sleep on this more before I blog about the bigger picture.” I don’t think I’m ready to do it with the right perspective yet. (Translation: I’m still a little disappointed, heh.)
This has inspired me to change ALL my passwords since there were a few sites where I hadn’t changed my password in over a year. That has been remedied as of now.
Great! That’s a smart action to take.
“Who you should blame …”
“Who you should not blame…”
Wow really? I hope that was tongue in cheek.
Dan – bingo. 😉 As you may have picked up by now, I have a slight sense of humor. Just a bit though.
‘your ancient SQL Server 2000 in the corner where everybody knows the SA password’. Well, if it were one of the previous versions the password would be blank, (the default setting) but in the case of 2000 it will probably be ‘password’. We are, after all, professionals.
Hahaha, yep!